Coinomi Addresses Spellcheck Vulnerability, Accuses Victim of Bitcoin Extortion

A vulnerability in crypto wallet Coinomi is causing concern. | Source: Shutterstock
CCN.com earlier reported that Coinomi wallet had a confirmed bug that allowed Google to view the details of a user’s seed phrase. The seed phrase generates a wallet. Coinomi uses a 24-word phrase. It enables a user to regenerate their wallet on any platform, and maintain a simultaneous wallet on their phone and on their desktop.
According to Coinomi’s own blog post on the subject, CCN.com and social media users wrongly characterized the transmission of seed phrases.
Packets Were Not “Plain-Text”
For one thing, the transmission was not intentional or by design. The bug only affected desktop wallets. The error happened because of a plug-in used in the desktop wallet. The team in charge of that plug-in had pushed a patch fixing the error on the same day Coinomi first heard of it.
The user claims the packets were “plain-text.” But the alleged victim’s own screenshot shows encrypted packets:
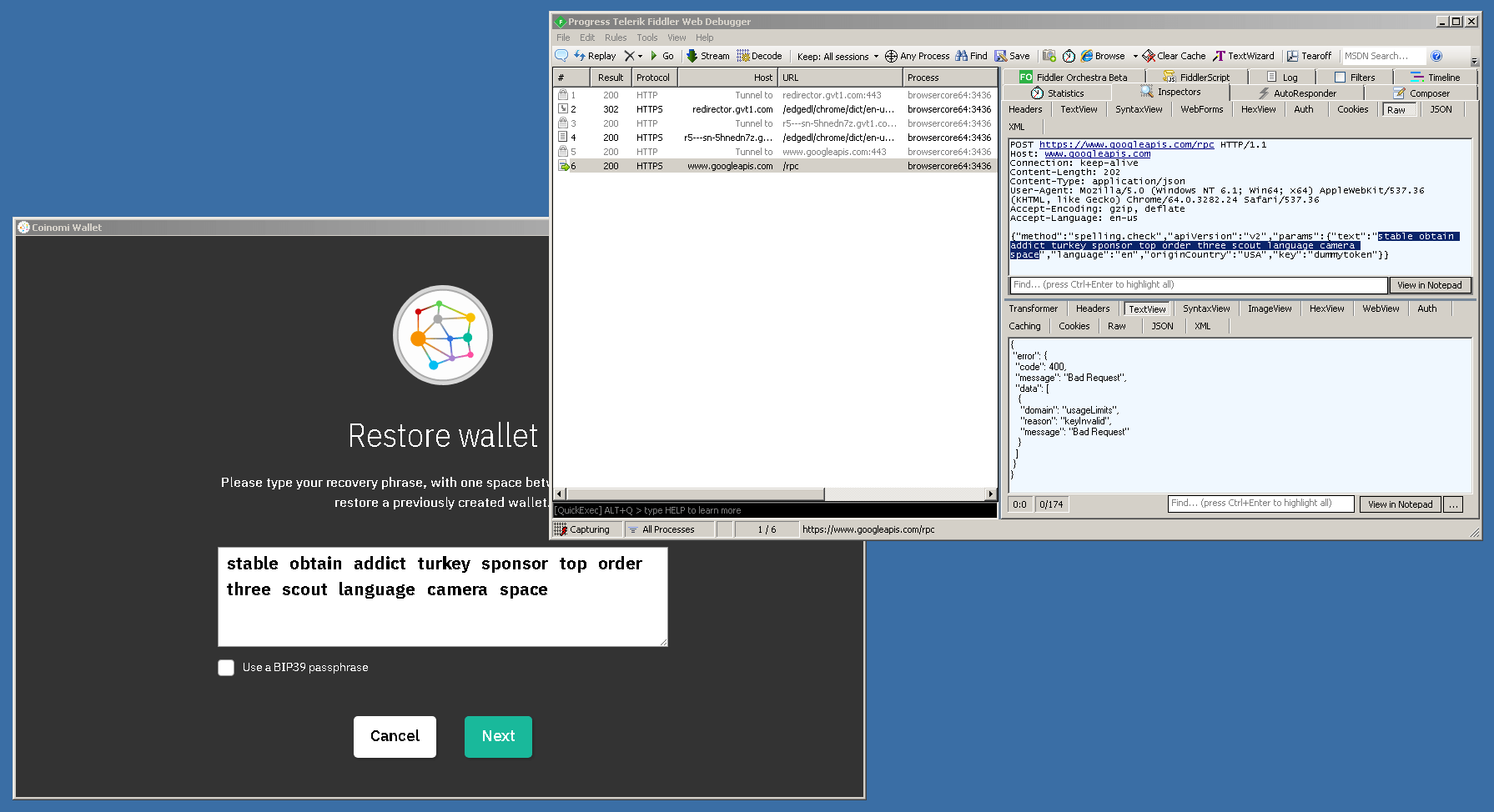
Perhaps most importantly, Google rejected the malformed requests. Coinomi explains this in their own addressing of the issue:
The spell-check requests that were sent over to Google API were not processed, cached or stored and the requests themselves returned an error (code: 400) as they were flagged as “Bad Request” and weren’t processed further by Google. […]
User Demands 17 BTC From Coinomi
Coinomi goes on to disclose the tactics used by the alleged victim, Warith Al Maawali. Al Maawali has not published blockchain evidence of the funds moving anywhere, but he has demanded that Coinomi pay him 17 BTC. Al Maawali writes in his Reddit post :
On 22nd February 2019, I noticed that more than 90% of my Exodus wallet assets were transferred to multiple wallet addresses and the first transaction began with BTC on 19th February 2019 around 3:30 am UTC. Then followed by ETH (including ERC20 tokens), LTC and finally BCH.
Again, the statement comes with no evidence, despite the user providing evidence of most of his other claims. Coinomi responds to this by saying:
During these days, Warith Al Maawali repeatedly refused to disclose his findings and kept threatened to take this public if we didn’t pay right away the ransom of 17 BTC which would make up for the “hacked” funds (stolen by Google, according to Warith Al Maawali) that are possibly still controlled by him […]
Coinomi acknowledges that there was a bug, but they don’t believe it actually lead to the loss of any funds. An attacker would need access to Google’s encryption suite. Al Maawali says he will begin pursuing legal action. He will have to produce proof of the funds moving on the blockchain. This would help amateur and professional sleuths track them down. Finding the culprit would help everyone better understand what actually happened.
Coinomi’s Handling Could Have Been Better
Still, Coinomi’s behavior towards the user is questionable. As Al Maawali writes:
They kept ignoring my request of taking the responsibility and ignored my solid facts regarding it. They didn’t give a single **** about my stolen crypto assets. [K]ept reminding me (kinda threatening me) of the legal implications if I go public with the information I have and they forgot their legal responsibility for my stolen crypto assets as well as the risk that impacts other users of the wallet.
He also posts a number of since-deleted tweets from the Coinomi team .
We cannot determine whether or not funds actually disappeared. We have to wonder why the victim failed to provide blockchain proof of the funds moving. Being a highly technical user, he should understand this would be critical in making his story believable.