Cryptojacking is Dying, But What’s Coming Next is Even Worse

For better or worse, bitcoin is now on the global stage, and the cryptocurrency could face a war for its very survival. | Source: Shutterstock
With shrinking profit margins and the closure of Coinhive, cryptojacking looks like it’s coming to an end.
The in-browser Monero mining program was conceived as a means of legitimately monetizing web pages. Instead of plastering a web page with ads, the mining software harnessed a fraction of the computing power of each site visitor.
The more people visited a site, the more processing power was siphoned to mine Monero, allowing site owners to profit without advertisements.
Cryptojacking: Rise and Fall

Source: Pixabay
In theory, not a bad idea. In practice, the software went on to form the foundation of the notorious cryptojacking malware that ended up affecting millions of user devices, spiking electricity bills, and draining batteries to secretly and illicitly mine cryptocurrency.
Affected users typically are not aware that their device has been hijacked to mine Monero, making it an appealing crime to cybercriminals looking to fly under the radar.
As more and more criminals hacked sites and planted the Coinhive file configured to mine Monero to their accounts, the issue skyrocketed out of control.
Cryptojackers targeted government websites, shut down university networks, and hit so many sites that Google banned all crypto mining extensions from the Chrome store. Even the legitimate ones. Cryptojacking rose by 459% in 2018, thanks in part to an NSA leak.
Software known as Eternal Blue was leaked from the NSA and sold online by a group called the Shadow Brokers. The leak enabled more hackers to exploit vulnerabilities in Windows-based systems, perfect for cryptojacking.
The problem grew out of control.
Coinhive was listed as the world’s greatest online malware threat by cybersecurity firm Check Point for 15 consecutive months, and an estimated 5% of all Monero was mined through cryptojacking .
https://twitter.com/bad_packets/status/1030201187381927936
However, as the profit margins of Coinhive – the legal browser extension – shrunk, so too did those of the cybercriminals.
Coinhive Shuts Down

Coinhive announced last month in a blog post that it would be shutting down, citing the decline in the crypto market as well as the drop in the Monero hash rate.
“Some of you might have anticipated this, some of you will be surprised. The decision has been made. We will discontinue our service on March 8, 2019. It has been a blast working on this project over the past 18 months, but to be completely honest, it isn’t economically viable anymore.”
“The drop in hash rate (over 50%) after the last Monero hard fork hit us hard. So did the ‘crash’ of the crypto currency market with the value of XMR depreciating over 85% within a year.”
“This and the announced hard fork and algorithm update of the Monero network on March 9 has lead us to the conclusion that we need to discontinue Coinhive.”
The decision was foreshadowed by reports from the intelligence community that cryptojacking was turning less of a profit from 2018 onward, with one report stating that a major attack hijacking 5,000 different websites only mined $24 worth of Monero .
As cryptojacking software is typically just a modified version of Coinhive installed as malware, it stands to reason that hackers are facing the same problems and that cryptojacking is to become a thing of the past. But the hackers are far more likely to turn to other methods rather than retire.
If cryptojacking is dying, what will replace it?
Crypto Malware: The Second Wave

Though Coinhive is shutting down, cryptojacking is still ranked #1 in terms of global malware threats. Meanwhile, there are a number of other contenders for the throne vying for power.
Threat Intelligence Lead at Proofpoint security company Chris Dawson pointed out that Coinhive was far from the only cryptojacking malware on the market, adding that the fall of Coinhive leaves a power vacuum waiting to be filled.
Coinhive accounts for around 60 percent of the cryptojacking market — which means there are 40 percent which are others already in use, so we’ll probably see a spike in those.
Other experts, however, view the entire cryptojacking trend as increasingly dated, with Jerome Segura of Malwarebytes telling ZDNet that the criminal industry is slowing down.
There are still a lot of hacked sites with Coinhive code, but I have a feeling these are mostly remnants from past hacks. Most of what I see these days is CoinIMP [a Coinhive competitor] and it’s been active again with Drupal hacks recently. But overall, I think the trend is nearing out.
Proofpoint’s Dawson conceded that the true threat would now come from other forms of malware.
Mining was an easy add on. Now we’re seeing a shift away from that towards banking trojans, credential stealers, pieces of malware which sit on machines.There’s continued ebb and flow of the malware we’re seeing and things like EternalBlue are out there and until we’re robustly patching, we’re going to continue to see threat actors trying to exploit that.
Top Threats
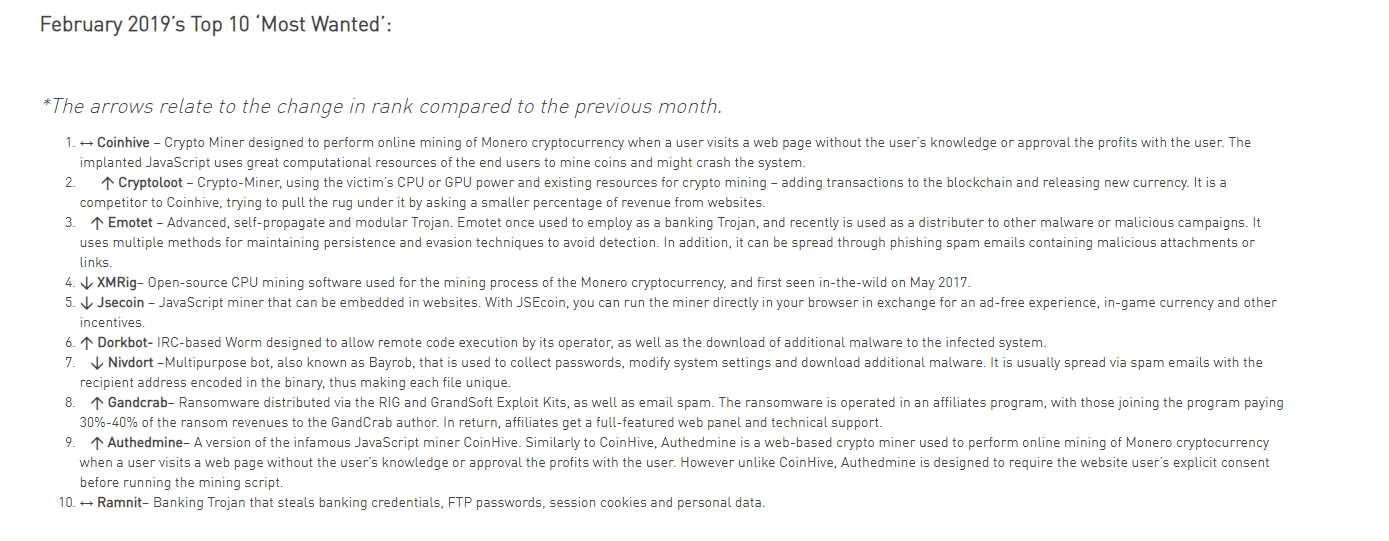
According to Check Point , the second “most wanted” malware program is also a cryptojacking tool called Cryptoloot, a rival of Coinhive gaining a competitive edge by seeking a smaller profit from each site.
After that, we have Emotet, a banking Trojan (malware masquerading as another program) which can infect a computer as a malicious attachment and be used to spread other forms of malicious software. The fourth spot is yet another mining program, Jsecoin, as is the program in ninth place.
The rest of the list is occupied by Trojans, password-collecting bots, and ransomware, or software which encrypts files and hard drives and demands a ransom in exchange for the release of the data.
Ransomware such as WannaCry and the more-advanced Petya has wreaked havoc over the last few years, taking down services at hospitals, car factories, government facilities, and airports as well as infecting personal devices, all in order to exact a ransom usually payable in Bitcoin.
While the closure of Coinhive is seen as a victory for some, the fact remains that malware is becoming increasingly more sophisticated and dangerous over time. A few years ago, the damage wrought in the last few years by malware would have been unthinkable.
It stands to reason that the programs that will follow are likely to be even more catastrophic.
Malware typically infects a computer when the user clicks on a malicious link or downloads a suspicious file. With the rise of malware affecting more and more users, computer security and personal vigilance are more important than ever before.