How CTB-Locker Ransomware Uses Bitcoin And Blockchain

Why is ransomware the new rage? Denis Sinegubko, the founder of Unmask Parasites and senior malware researcher at Sucuri, a network security firm, notes in a Sucuri blog that the answer to this question has to do with the way ransomware demands are paid.
Unlike false anti-viruses that were mostly harmless and made people pay to remove non-existing threats, ransomware is a more serious challenge since it disables the computer unless a ransom is paid.
Ransomware schemes were not available five to eight years ago. Ransomware could not accept PayPal or credit cards since those transactions are traceable. Cryptocurrencies were not an option since they were not established. Even after bitcoin emerged in 2009, it took a few years for it to build an ecosystem and achieve the adoption that made using them worthwhile.
Mass adoption of bitcoin has brought new types of criminal schemes.
Hackers are currently expanding ransomware from local computers to websites. Things like DDoS attacks that encrypt websites and extort bitcoins as ransom have become more common.
Enter CTB-Locker
The CTB-Locker ransomware is currently attempting to enter the website ransomware niche.
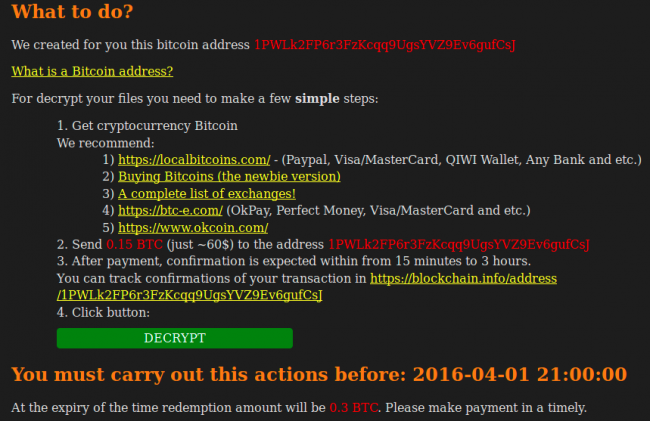
In February, the following message appeared on encrypted websites.
The ransom is 0.4 BTC if paid immediately and 0.8 BTC if paid in a few days. The price is higher than a typical fake anti-virus, which is $40 to $90, but much lower than the 3 BTC that CTB-Locker asked on encrypted PCs. It is also less than the 1 BTC demanded on encrypted websites in December 2015.
In March, the CTB-Locker message looked as follows:
In one month the ransom fell from 0.4 BTC to 0.15 BTC and from 0.8 BTC to 0.3 BTC for late payments. This “website ransomware” more closely resembles “scareware” than the desktop version.
Other changes have occurred between February and March versions of CTB-Locker for websites.
How It Works
CBT-Locker encrypts two random files with a separate key and enables the victim to decrypt them for no pay to demonstrate its functionality.
This serves to build confidence that following payment, the website can be restored. But this feature changed in March. 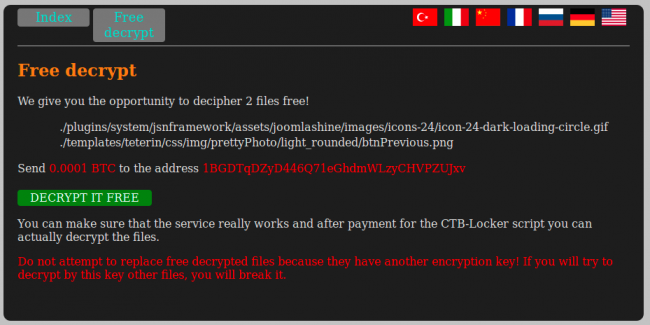
It looks similar until you see that the “free” test now costs 0.0001 BTC.
Why do they ask for the small fee? First, consider an internal change in the March CTB-Locker version.
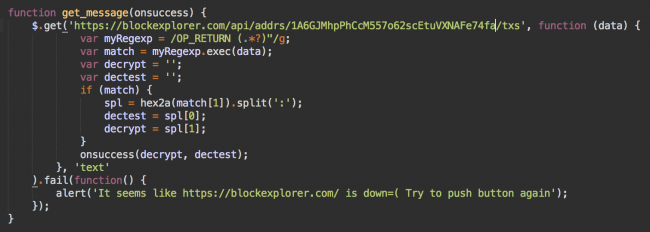
The February version shows that successful decryption requires the access.php scripts on around 100 third-party “gate” sites. But it’s not a reliable approach. The gate sites are also hacked so that the access.php script can be removed at any time. To improve chances the decryption script works using a live gate, each script needs a list of three random, predefined gates.
admins = [“hxxp://stian .malkenes .com/access.php”, “hxxp://autobot .sk/access.php”, “hxxp://cresynin .com/cgi-bin/access.php”];
But these cannot guarantee the site can be decoded following payment. The issue with this unreliable intermediate layer has been solved in the March CTB-Locker version. It is based on blockchains.
What Blockchains Bring
Blockchains are verified transaction chains. They cannot be tampered with.
Every bitcoin transaction gets recorded in the distributed blockchain database.
Send bitcoins to a wallet and if the owner of the wallet spends the money, it will record on the blockchain.
The blockchain database is public so that everyone can see all the transactions.
There are public services that allow anyone to view bitcoin blockchains. Two such services are blockchain.info and blockexplorer.com, both of which CTB-Locker uses.
Each blockchain record has all the information about the transaction, including wallet addresses, sums and time stamps linked to the transactions.
The bitcoin protocol was extended in 2014 so that transactions could include small blocks of arbitrary text in the OP_RETURN field, making it applicable to fields not related to bitcoin.
Most bitcoin transactions incur a minimal 0.0001 BTC fee.
Hackers Create Bitcoin Addresses
For every encrypted website, a hacker creates a new bitcoin wallet with a unique address they publish on the page demanding a ransom. The hacker creates an address for the bitcoin ransom.
When the victim pays the ransom by sending the 0.0001 fee for the decryption referred to as “free,” the hackers check the sum. When they see the 0.0001 BTC fee, the wallet’s blockchain updates with a transaction in which the OP_RETURN field has the decryption key for the two free test files. When the victim pays the complete price, they add the transaction with the keys for the remaining encrypted files.
The hackers can’t just append the OP_RETURN transaction to a wallet that is empty without revealing their own wallet. In addition, they have to pay the 0.0001 BTC fee for the transaction. This is why they tell victims to transfer a minimal fee for the “free” decryption test. It is this transfer that creates a blockchain for the wallet and covers the fee for the OP_RETURN transaction.
The 0.0001 BTC fee is not a barrier for the “free” test since it is a small amount of money and those who want to decrypt their sites will have bitcoins.
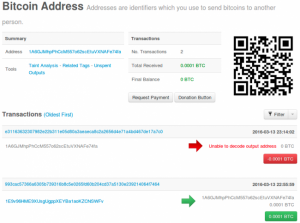
A few minutes later, the OP_RETURN transaction is validated and advances through nodes of the bitcoin system and is visible in blockchain information services. Below is a real “free decrypt” blockchain for an affected site.
The first transaction (green) sent 0.0001 BTC to the address on March 13 at 22:56. The second one (red) sent the same amount 20 minutes later. By clicking on the red transaction link, the transaction fee was 0.0001 BTC with the OP_RETURN that decodes the address. In this value, the text before the colon is the decryption test key while everything after the colon is the full site decryption key.
Because it was a 0.0001 BTC transaction, the OP_RETURN has only the “free” decryption test key.
The CTB-Locker script prefers working with a computer-friendly version offered by the API on the blockexplorer.com site.
The March version of the CTB-Locker reads the keys right from public and more readable blockchain information services. With bitcoin transactions, everything is transparent and public. It is possible to keep things anonymous.
Also read: Cryptocurrency for ransomware may fuel “largest crime wave in modern history”
CTB-Locker Is Not A Success
But the CTB-Locker website version can’t be called successful. They lower their ransoms because webmasters don’t pay them. The model working for PCs does not work for websites. When CTB-Locker encrypts a PC, the user loses files and content. In the case of both encryption and disk failure, the cheapest recovery solution provides a fresh external backup.
The website ransomware is closer to “scareware” that attempts to trick the webmaster to pay for a service they don’t really need.
Sinegubko googled the sites encrypted by the CTB-Locker and checked the transactions for each bitcoin address published on the demand pages. Out of nearly 100 sites, only one contained a real “free” decryption test 0.0001 BTC transaction. Bitcoin wallets for the rest of the encrypted sites had no transactions. The investigation found none of the webmasters paid the ransom, and most were able to recover their sites.
New technologies change our lives, but they also bring new threats. Ransomware has gone mainstream due to bitcoin and blockchain.
Featured image from Shutterstock.