Zero Customer Knowledge VPNs
 Thanks to Operation Onymous there has been a great deal of attention on anonymity networks. There are three major networks out there and a fourth hybrid has just popped up in response to some troubles affecting Tor, the largest and best known of the three.
Thanks to Operation Onymous there has been a great deal of attention on anonymity networks. There are three major networks out there and a fourth hybrid has just popped up in response to some troubles affecting Tor, the largest and best known of the three.
These networks are:
- @torproject : Originally an effort of the U.S. Naval Research Lab , then later fostered by the Electronic Frontier Foundation, this is the largest of the three.
- @i2p : An independent project, I2P offers a network interface similar to Tor, and it suffers the same SOCKS5 related vulnerabilities recently described in Operation Onymous & Tor Security
- @Cryptostorm_is is a grassroots project, the successor to Cryptocloud, which was preemptively dismantled by the operators after the Snowden leak but before the NSA could get to them. They use OpenVPN for transport, and much of their innovation is in the compartmentalized structure and Zero Customer Knowledge provisioning they do.
- @Torstorm_org : An internal service of Cryptostorm, this is a brand new effort to institutionalize what skilled operators have long done – ensuring that attacks on browsers accessing Tor sites produce no usable information for the opponent.
Tor Project
The Tor Project provides a local behind the scenes application that offers an SOCKS5 proxy service for browsers, chat clients, and anything else that will run over the virtual circuits provided by the Transmission Control Protocol . There are provisions for hidden services that are named using .onion addresses. There are not provisions for the datagrams that ride in User Datagram Protocol , which means things like DNS name services and streaming audio are not supported. The de facto leaking of those two protocols has been used to identify Tor users and sites.
The core development team was originally funded by the Navy, and funding sources evolved as the network grew. There is no revenue model for entities that either provide transport via running relay nodes or provide access to the clearnet via exit nodes.
I2P
I2P started as a one man band, with some good ideas and a community has grown around it. There is no funding. The user facing portion of the service is like Tor, an SOCKS5 proxy, there are hidden services, and there are types of nodes that provide clearnet access, but in general I2P users are expected to stay within the system. The culture is very much that of the pre-web internet, smart, quirky, and mostly friendly.
This network is neither fast enough nor stable enough for a darknet market to emerge within it, but it hosts a vibrant IRC chat network and there are committed core developers. They benefit from the inclusion of their software in TAILS , the privacy focused Linux distribution favored by Edward Snowden and Whonix , a dual virtual machine Linux gateway/workstation system favored by those who operate in high threat environments.
Cryptostorm
An effort by hardcore cryptography & privacy activists, this network has termination points in Iceland, Germany, Portugal, and there are rumors of additional countries in the works. Connections are made via OpenVPN , which is valued for its sturdy, simple configuration, rather than IPsec, which is notoriously difficult to make behave. This one stands apart from the other major anonymizing networks in three important ways. Access is implemented via an anonymous token rather than through the creation of a username/password pair associated with a subscriber account. The tokens are sold and the network is a self supporting entity. Being a VPN rather than an SOCKS5 based service this network can support streaming UDP applications.
The two innovations of this admittedly feral service provider are their Zero Customer Knowledge provisioning and their focus on creating a decentralized, loss resistant architecture.
Torstorm
This is a brand new thing from Cryptostorm, just a few days old. It’s not entirely clear what the final destination will be, but the starting point is fairly impressive.
First, they’ve launched a service similar to the Tor2Web clearnet to Tor hidden service proxy. If you visit https://agorahooawayyfoe.torstorm.org you’ll see https://agorahooawayyfoe.onion, the Agora darknet market hidden service page. This only works for Cryptostorm customers, but you can visit Cryptofree , and receive a free tokenless low speed connection to their network so you can see for yourself.
Skilled users are already making a VPN connection from their workstation or network edge, then accessing Tor from there. This is done to ensure that any adversary who can break their browser will face a VPN provider subpoena before they get an actual IP address, and Cryptostorm’s anonymous access tokens means they are a dead end for such efforts. Torstorm looks to be a fundamental advance, reducing a complex set of inter-related problems into a single purchase of a simple, well-documented service.
A Surveillance Nightmare
The reason Cryptostorm can use the same protocol as all the other VPN providers and has never once given up any customer information has nothing to do with protocols and everything to do with the temperament of those running it. The group will not confirm or deny that anyone works there but in talking with the anonymous personas it’s clear they’ve all had some involvement in darknet markets or hacktivism. Cryptostorm exists as it is because all parties involved have a deep, personal understanding of what happens when things go wrong.
The server locations are known, the software is open, the configs are published, there are voluminous notes about why things are the way they are, and authorization is via a decentralized datastore . If someone’s house gets raided and all their electronics are taken away, the network will continue to run. If a given datacenter is compromised and the machines are carted away the network loses capacity, but there is nothing present that would give any information on customers; they just start over at a new location.
Cryptostorm occupies a very specific niche, appealing to a class of customer that is highly unlikely to trust anyone else. They think the concept is bigger than what they are able to execute and, having abided by open source software principles, they expect someone to come along and pick their pockets for intellectual property.
Enter Ethereum
 The Cryptostorm model works well for the dirty end of the field, but what about the rest of us? This is where the concept of Decentralized Autonomous Corporations come into play. The Coinwiki.info entry is fairly succinct.
The Cryptostorm model works well for the dirty end of the field, but what about the rest of us? This is where the concept of Decentralized Autonomous Corporations come into play. The Coinwiki.info entry is fairly succinct.
A Decentralized Autonomous Corporation (sometimes referred to as a Fully Automated Business Entity or a Distributed Autonomous Corporation, often abbreviated “FAB” or “DAC”) is a decentralized (or distributed) network of narrow-AI autonomous agents which perform an output-maximizing production function and which divides its labor into computationally intractable tasks (which it incentivizes humans to do) and tasks which it performs itself. The Ethereum blockchain has specific features meant to facilitate this.
An Etherum blockchain can play host to such an entity. The rules of its operation are created, and once launched it continues, but only so long as it provides value and people (or other DACs!) are willing to use it. Instead of a group of shadowy individuals, an open set of business rules would define the service. Here are some features we should expect to see:
- Access will be by anonymous tokens, produced within the blockchain itself.
- Servers providing direct internet access & Torstorm will be run by the DAC’s creator.
- VPS vendors could agree to host ‘onramp’ nodes, providing entry points to the anonymizing network by using their off hours capacity.
An Example Decentralized Environment
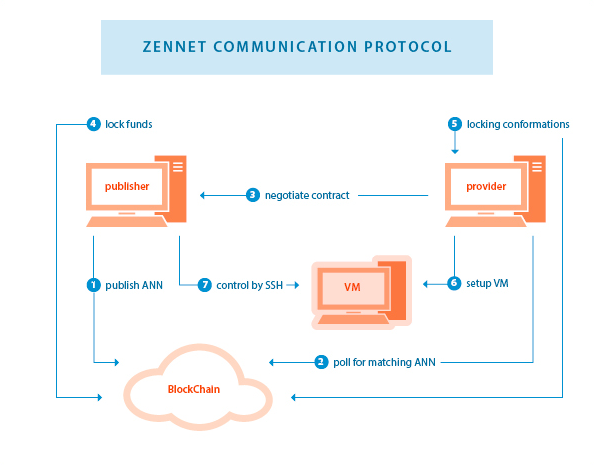
As Cryptostorm serves as a profitable pilot project for Zero Customer Knowledge VPNs, the Zennet Supercomputer serves as an example of how spare network capacity on virtual private servers could be brokered to a VPN provider to offset costs.
The major components in the Tor network are hidden services, exits to the clearnet, and relays. A hidden service can get raided if it’s hosting illegal content, exit nodes are often harassed with DMCA takedown notices for torrent content, and Tor exits are frequently banned by some types of businesses. A VPS operator willing to terminate inbound OpenVPN connections would be in a similar role to a Tor relay operator.
An Immediate Opportunity
Cryptostorm already runs, runs well and has for years. Ethereum has taken in $20 million in investment and if not them for the blockchain technology there are other efforts such as Counterparty that offer similar capabilities. Zennet Supercomputer shows a business model that could be used to more broadly distribute connection points for the service, an interesting concept, but one that requires much more thought before making such a thing part of an anonymity network.
Cryptostorm’s current methods cure for several of the defects in Tor and with Torstorm they offer the best of both worlds. They already share much of their software and methods via their forum and would not be opposed to other vendors cloning their effort. An investor willing to fund a legal and operational review could very quickly turn up a cash flow positive prepaid service. Given the wave of privacy concerns in the world today this is liable to happen very, very quickly.
(Full Disclosure: I am one of the people working the booth for Several Startups at the CryptoMoneyExpo on December 5th and 6th. Cryptostorm is among the companies represented.)
What do you think of these new privacy solutions? Comment below!
Images from Cryptostorm_is, Ethereum, Zennet and Shutterstock.