Op-Ed: Bitcoin Security — How Do We Arrive at Consensus?

If the title sounds confusing, that’s not surprising. I was trying to get creative and find a set of words that could express how I perceive most will react upon learning the theme of the article.
For what I want to discuss with you guys today is a hotly debated topic.
One that might shake the grounds of cryptocurrency’s inner-working mechanics: which consensus algorithm is better, Proof-of-Work (PoW) or Proof-of-Stake (PoS)?
PoW vs PoS vs DPoW vs DPoS
PoW and DPoW represent the same way of mining, in terms of infrastructure, but in different organizational formats. The first assumes one person or company is the owner of the hardware. The second assumes a network of people giving their computational power to a central authority who mines on their behalf. And then you also have cloud mining.
There are other ways of mining, such as through mining contracts where you purchase some of the hashrate from a mining farm, but I will ignore those as they simply represent a loan of equipment (like a lease).
What About Ownership?
If we consider the working mechanics of the “D” (delegated) in both PoW and PoS, it simply means you relinquish your right to control your hashing power, in order to gain more profits – as mining through a pool is considerably more profitable than mining by yourself (if you cannot invest much in equipment, that is); because mining pools have more hashing power, you’ll get bitcoin block rewards and transaction fees more often, although the prize is split among more participants.
For this article’s purpose, I will make two assumptions:
(a) Our goal is to focus on network security; hence the best consensus algorithm will be the most secure.
(b) For analysis coherence, ownership of hardware is always preferable due to fewer dependencies.
By combining both assumptions, we can already pen down a quick conclusion.
The Ultimate Battle: PoS vs PoW
If ownership is always preferable, we can assume any option where a user relinquishes power over decision-making, is tilting his goals towards profits. Therefore, his values are not the same as the ones of other miners: to secure the network.
If the real battle is between owners of hardware, we can eliminate any delegated system, as there is a central point of failure.
In different systems, we can add extra layers like many delegates, although the core issue remains: authority is not properly distributed because delegates can easily collude to stay in power.
If one party has the option to easily make changes to a network, there is a central point of failure, which should be avoided at all costs, not only to preserve decentralization but to guarantee the network’s permissionless nature.
Security And Speed
We can then limit our decision to either PoW or PoS. Both have advantages over each other, but ultimately, one should be safer than the other.
Ultimately, decision-makers might choose either,depending on the end-goal: security or speed? Robert Greenfield from ConsenSys explains this dilemma quite well:
-
PoW — The process of solving a computational challenge imposed by a proof of work protocol is called (block) mining. It has an objective consensus protocol, where a new node can independently arrive at the same current state as the rest of the network based solely on protocol rules.
-
PoS — The process of solving a computational challenge imposed by a proof of stake protocol is called (block) minting. It is not an objective protocol. It is weakly subjective, given that a node needs a recent state in addition to protocol rules and messages propagated across the system to independently determine the current state of the system.
The Arguments Against PoW
Most people point out the worst aspect of PoW is how it wastes energy to mine new blocks, however, given my approach to the topic I would prefer to focus on alternative attack vectors, as to me there is actually no energy waste – if we compare the Bitcoin infrastructure with the global gold infrastructure, we can quickly conclude Bitcoin is spending 10% or less than its physical counterpart. Plus, the number of users is not correlated to the number of miners, meaning more Bitcoin users doesn’t equal more miners.
What other problems can we look into?
- DoS Attacks — A DoS attack aims at disrupting the normal operation of the network by flooding the nodes with requests (PoW is more vulnerable to this situation).
- Sybil Attacks — The attacker disrupts the network by forcing a number of nodes to misbehave. (again, PoW more vulnerable to this type of attack).
PoW is indeed weak against those two types of attacks, and we’ve already seen some networks being hijacked by both.
Plus, PoW is a slower process for consensus. If we’re not talking about a layer 1 solution (like Bitcoin), we can potentially forego security for speed by adjusting how network reaches consensus.
Instead of doing hard computations why not ask network validators to stake some of their coins, in proof of good faith?
The Arguments Against PoS
While in a PoW network, the system is divided among miners, developers and other crucial members of the community, on the other hand, in a PoS network stakeholders have the power to make any changes they see fit, without the full consent of the community, businesses, miners and developers.
This centralization of voting power and control of the network defeats the purpose of a distributed ledger-based cryptocurrency, since it contradicts its entire principle of distributing all elements within the network, to diminish the presence of a central authority and a central point of failure.
51% Attack
Considering the bottlenecks and merits of both PoW and PoS systems, the latter seems more prone to centralization – which is what a cryptocurrency network must avoid at all costs. Despite its advantages in preventing the 51% attack, PoS brings its own risks, which should be avoided by a truly decentralized network. One type of attack easily executable in PoS, which is harder to execute in PoW (if not impossible in larger networks like Bitcoin) is a bribe attack :
- Initially, the attacker performs a spending transaction he later wishes to reverse,
- Immediately after, the attacker secretly builds a chain based on the block prior to the one containing the transaction.
- When the transaction gets the necessary number of confirmations and the attacker’s chain is longer than the valid chain, the attacker publishes it as a whole.
- The new chain is accepted as the valid blockchain, and the transaction is, thus, reversed.
Nevertheless, PoS enables the development of faster consensus algorithms, as no energy is required to provide proof-of-work, meaning, quite easily a protocol can scale the number of transactions per second, or to add new staking nodes just by lowering the stake required.
The key difference is that PoS enables higher throughput and performance, enabling further use-cases.
The Ultimate Tie-Breaker: Network Security
At the beginning of the article I made two assumptions, one of which was a shout-out to focus our needs in securing the network.
Speed and exchangeability are incredibly important features, that should come after we’re sure we’re relying on a safe infrastructure that cannot be changed or manipulated.
To me, without question, PoW is the most secure consensus mechanic out there, and we shouldn’t aim at replacing it so soon.
The discussion around efficiency doesn’t really matter for the security layer. We want an effective network, not an efficient one.
Security > Speed
The fact that tons of energy are spent just to secure the Bitcoin network should definitely make most of us happy.
It means whoever wants to attack the network needs to spend that same amount of energy to re-do all work done.
Yes, it becomes quite literally impossible to change the past!
That connection does not exist when we consider PoS systems. Because users are not doing any work to find a hash, there is no real cryptographic security, as energy isn’t spent by staking nodes. The only thing an attacker needs to do is to purchase enough coin to perform a 51% attack.
Does it make sense to have PoW applied to every single cryptocurrency infrastructure?
Speed & Interoperability
One of the key arguments for cryptocurrency adoption is the need to make the system way faster and easy to use. Besides way better UX/UI, we definitely need to focus on building scalable systems, with scalable infrastructures and consensus mechanics.
If you’re looking to learn more about live use cases of PoS, my advice is to look into projects that properly use this technology.
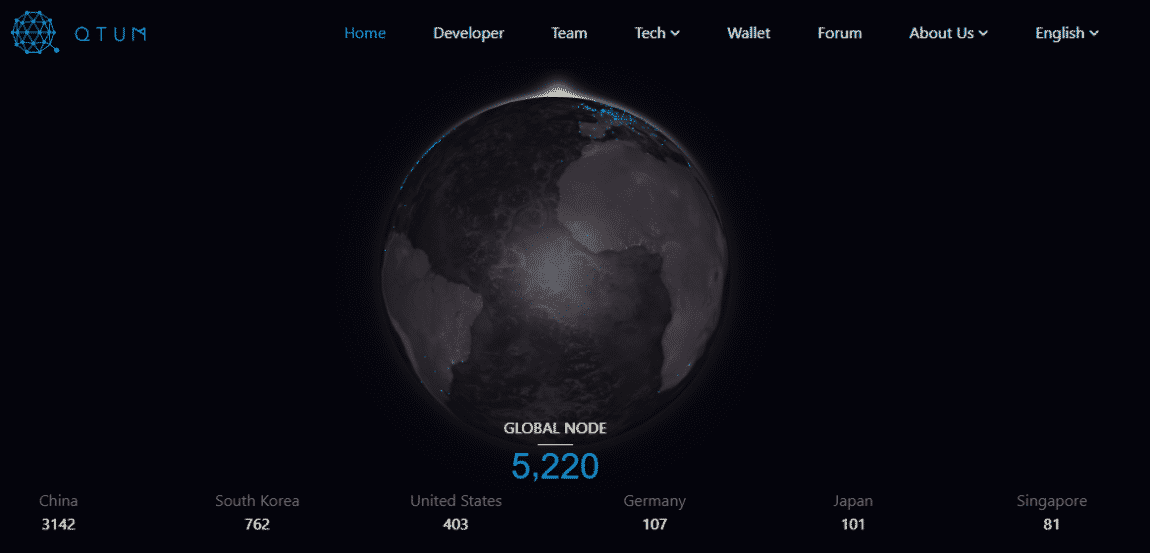
One of my preferred examples is QTUM; it’s actually using a PoS consensus algorithm in a live, decentralized, permissionless protocol, which can be mined by anyone staking 1 QTUM or more. Better yet, it currently has more than 5,000 active nodes spread across 3 continents.
I love the idea of decentralization, meaning, I truly believe having multiple layers with alternate purposes is how cryptocurrencies will eventually develop, as each layer is expected to perform different tasks.
We can have a central protocol to deal with money, plus others to deal with smart-assets in multiple industries such as supply chain, gambling , land registry, and so on.
If we bet on many integrated protocols, very good at doing a specific task, we’ll be adopting a past strategy that seems to have worked. Just look at hardware components and IoT devices!
Small protocols will pave the road to adoption, I argue, all integrated and working together to achieve the same goal.
In a sense, by having many components working towards the same goal, it becomes easier to work on each separately; if rightfully implemented (for instance, by having Byzantine fault tolerance), even when one component breaks, the system as a whole still functions.
That’s where I see crypto-projects heading: into a future of cooperation, as well as competition.
Thanks for reading!
Leave your comments and thoughts down below.
Disclaimer: this article isn’t financial advice; it represents my personal opinion and should not be attributed to CCN.com. I have savings invested in cryptocurrency so take whatever I write with a grain of salt. Do not invest what you cannot afford to lose and always read as much as possible about a project before investing.
Featured Image from Shutterstock