New Malware Mines Bitcoin via Victims’ CPUs and GPUs

Palo Alto Networks has discovered a unique malware family that can mine bitcoins via the victim’s CPUs and GPUs. The malware, called PWOBot, is completely written in Python and compiled via PyInstaller, generating a Microsoft Windows executable, according to a Palo Alto Networks posting . The malware has affected European organizations, mainly in Poland. A Polish file-sharing service delivers the malware.
The malware can download and execute files, log keystrokes, execute Python code and mine bitcoins via the affected computers’ GPUs and CPUs.
The malware has been noticed as far back as late 2013. There are at least two variants. Recent attacks have affected organizations from mid to late 2015.
Numerous Victims Attacked
The malware has affected the following victims: a large Polish retailer, a Polish shipping company, a Polish national institution, a Polish information technology organization, a Danish building company, and a French optical equipment provider.
Chomikuj.pl, a Polish file sharing web service, downloaded most of the PWOBot samples. The following URLs have provided PWOBot copies.
s6216.chomikuj[.]pl/File.aspx?e=Pdd9AAxFcKmWlkqPtbpUrzfDq5_SUJBOz
s6102.chomikuj[.]pl/File.aspx?e=Hc4mp1AqJcyitgKbZvYM4th0XwQiVsQDW
s8512.chomikuj[.]pl/File.aspx?e=h6v10uIP1Z1mX2szQLTMUIoAmU3RcW5tv
s6429.chomikuj[.]pl/File.aspx?e=LyhX9kLrkmkrrRDIf6vq7Vs8vFNhqHONt
s5983.chomikuj[.]pl/File.aspx?e=b5Xyy93_GHxrgApU8YJXJlOUXWxjXgW2w
s6539.chomikuj[.]pl/File.aspx?e=EH9Rj5SLl8fFxGU-I0VZ3FdOGBKSSUQhl
s6701.chomikuj[.]pl/File.aspx?e=tx0a8KUhx57K8u_LPZDAH18ib-ehvFlZl
s6539.chomikuj[.]pl/File.aspx?e=EH9Rj5SLl8fFxGU-I0VZ3ISlGKLuMnr9H
s6539.chomikuj[.]pl/File.aspx?e=EH9Rj5SLl8fFxGU-I0VZ3OFFAuDc0M9m0
s6179.chomikuj[.]pl/File.aspx?e=Want-FTh0vz6www2xalnT1Nk6O_Wc6huR
s6424.chomikuj[.]pl/File.aspx?e=o_4Gk0x3F9FWxSDo4JWYuvGXDCsbytZMY
The IP address https://108.61.167 downloaded one instance of the malware. The address is related to the tracking[.]com domain, which a number of PWOBot samples also used.
The following file names delivered the malware:
• favicon.png
• Quick PDF to Word 3.0.exe
• XoristDecryptor 2.3.19.0 full ver.exe
• Easy Barcode Creator 2.2.6.exe
• Kingston Format Utility 1.0.3.0.exe
• uCertify 1Z0-146 Oracle Database 8.05.05 Premium.exe
• Six Sigma Toolbox 1.0.122.exe
• Fizjologia sportu. Krtkie wykady.exe [Physiology of sports. Short lectures.exe]
Samples Purport To Be Software
Some of the PWOBot samples present themselves as various software utility programs.
How the malware first infected its victims is unclear. The filenames allow some inferences since the malware could have gone to end-users thinking they were downloading other software. It is also possible phishing attacks enticed victims to download the files.
The attackers use PyInstaller to convert the Python code into a Microsoft executable. But Python, as it is being used, can move to other operating systems like OSX and Linux.
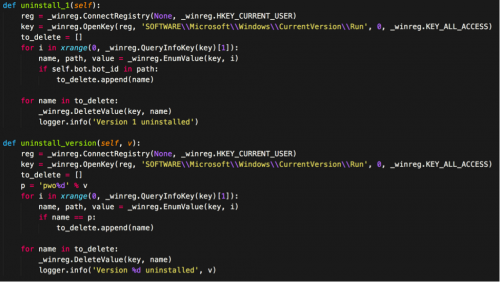
How It Installs
PWOBot, upon first execution, will first uninstall earlier PWOBot versions they find. The malware will query Run registry keys seeking previous versions. Most versions use a “pwo[VERSION]” format for the Run registry key, where [VERSION] is the PWOBot version number.
After the prior versions uninstall, the malware installs itself to create a copy of its executable in this location:
%HOMEPATH%/pwo[VERSION]
Then it sets the following registry key to direct to the newly-copied executable:
HKCU/SOFTWARE/Microsoft/Windows/CurrentVersion/Run/pwo[VERSION]
Should this be the first run for the malware, PWOBot executes the newly copied file in a new process.
Following installation, the malware hooks various keyboard and mouse events that are used for subsequent keylogging functions. PWOBot allows the attacker to include various modules during runtime since it is written in a modular fashion. The following services and their descriptions have come with PWOBot based on the samples currently identified:
• PWOLauncher : Download/execute file, or execute local file
• PWOHTTPD : Spawn a HTTP server on the victim machine
• PWOKeyLogger : Log keystrokes on the victim machine
• PWOMiner : Mine bitcoins using the victim CPU/GPU
• PWOPyExec : Execute Python code
• PWOQuery : Query remote URL and return results
Two Configuration Files
PWOBot comes with two configuration files, including one that specifies different settings the malware should use, while the other specifies the remote servers the malware should connect to during execution.

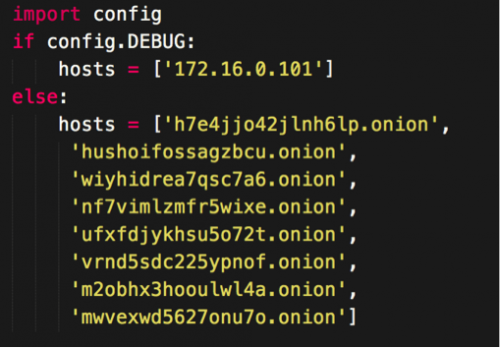
POWBot includes various windows executables included when attackers compile the code with PyInstaller, as shown in the settings configuration (Figure 2). The executables perform bitcoin mining and to-proxy requests via Tor. The bitcoin miner is a compiled version of cgminer and minerd. The files are used for CPU and GPU bitcoin mining respectively.
Also read: Report: BitTorrent malware risks call for better security measures
Malware Uses Tor
PWOBot uses Tor to tunnel traffic to attackers’ remote servers. This offers both anonymity and encryption, but it should also alert network administrators who see it since the traffic most likely violates organization policies.
PWOBot uses a Python dictionary for its network protocol. Every specified period PWOBot will notify the remote server.
Enumerations are configured to represent the different numbers encountered in the prior example. A more complete picture of the data being sent becomes visible when replaced with their respective enumeration.
Once notices are sent, the attacker might choose to give a command instructing PWOBot to perform a previously defined service. The results of these actions then upload to the attacker using the same format.
12 Malware Variants
A total of 12 malware variants apparently exist, based on the last versions Palo Alto Networks Unit 42 identified. The unit has witnessed versions five, six, seven, nine 10 and 12 in the wild.
Changes among versions seem minimal and are likely performance improvements.
While PWOBot has affected Microsoft Windows platforms, it can move to the Linus and OSX operating systems as the underlying code is cross-platform. This fact, along with a modular design, makes PWOBot a significant potential threat.
The malware family has not previously been disclosed.
Palo Alto Networks protects customers from this threat in the following ways:
• All PWOBot samples are properly categorized as malicious by the WildFire service.
• Domains related to the PWOBot threat have been appropriately categorized as malicious.
• AutoFocus customers may use the PWOBot tag to monitor this threat.
Featured image from Shutterstock.